Frequently Asked Questions for Microsoft Security Services
I have a cybersecurity incident. What kind of assistance can Professional Advantage help me with?
It is unfortunate that you are going through a cybersecurity incident. Our security services are not just limited to the prevention of a data breach or phishing attack, but we also assist with responding and recovering your data.
Please get in touch with us at 1800 126 499 or email us at [email protected] to get help from one of our cybersecurity experts.
What is the difference between Office 365 Security, Enterprise Mobility + Security, and Microsoft 365?
Office 365 already has basic security capabilities such as multi-factor authentication (MFA), data loss prevention (DLP), mail filtering, and anti-malware. E5 subscription also has eDiscovery, a stripped-down version of Advanced Threat Protection, auto data classification with Advanced Data Governance, and Office Cloud App Security.
Enterprise Mobility + Security is Microsoft’s mobile and security management platform composed of security solutions related to identity and access management, information protection, threat protection, cloud app security, and mobile security. These security products can be implemented on top of Office 365 and extended to your third-party software investments.
Microsoft 365 combines Office 365, Windows, and selected EMS features in one bundle. Depending on the plan you choose, the security features included in Microsoft 365 can be Advanced Threat Protection, Intune, Advanced Threat Analytics, Identity and Threat Protection, Azure Active Directory, Information Protection, and Azure Advanced Threat Protection.
How does Office 365 help me with compliance?
Compliance with government-mandated regulations such as the National Data Breach (NDB) and the General Data Protection Regulation (GDPR) is one of the major concerns of many businesses. Office 365, however, can be instrumental in complying with these policies. It already has built-in features that respond to the requirements of these regulations.
An example of this would be the encryption of physical disks; encryption of data at the application level; and encryption of emails and files in transit. It can also allow your IT to monitor and track user activities via the Office 365 audit logs. You can read more about how Office 365 helps with your compliance obligations in this blog.
Does Microsoft 365 include security?
Yes it does.
What is the minimum requirement for securing my Office 365 environment?
First of all, you need to assess how secured your environment is by checking your Microsoft Secure Score and taking necessary steps to improve it. You also need to turn on data loss prevention (DLP) and multi-factor authentication (MFA) when you deploy Office 365. We can guide you with the right combination of tools to help you protect your Office 365 environment. Visit this page to learn more.
If you are pressed for time or have limited knowledge or understanding of how Secure Score works, we can help you assess the security weaknesses in your Microsoft Cloud environment and devise a plan to reduce your risks by booking your Secure Score Analysis.
Alternatively, you can check out this blog on how to use Secure Score to improve your security posture.
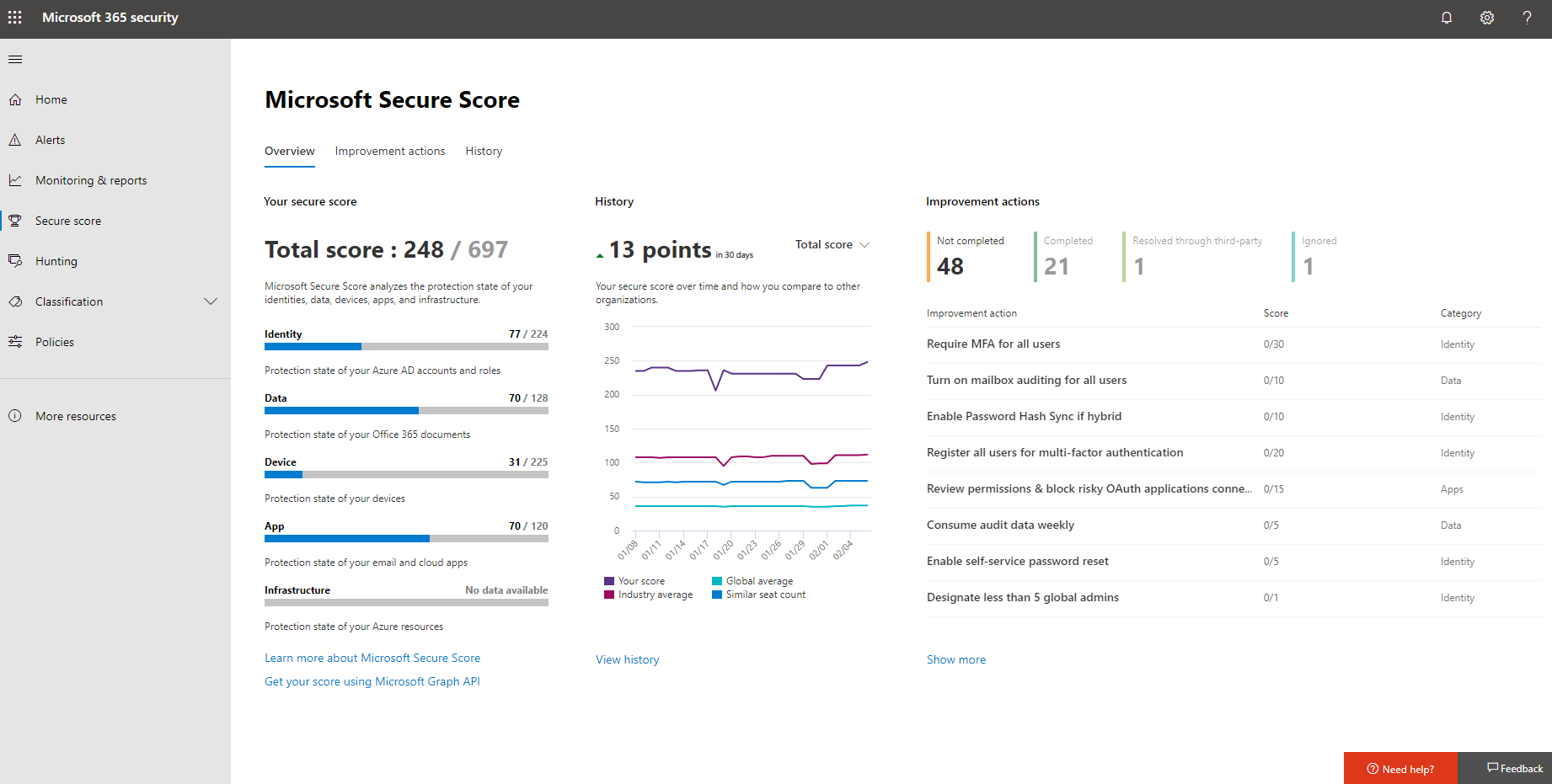
Source: Microsoft
What are the best practices for cloud security?
We recommend these five best practices to help you keep your data safer in the cloud.
- Strengthen access control.
- Improve security posture.
- Secure apps and data.
- Mitigate threats.
- Protect the network.
You can download the infographic in this blog to get a step-by-step walkthrough on how to protect your data in the cloud and learn how to identify security threats early.
What is a phishing attack simulation?
A phishing attack simulation is a controlled exercise conducted by an organisation to test and improve its employees' ability to recognise and respond to phishing attacks. These simulations are designed to mimic real-world phishing attacks, where attackers send fraudulent emails or messages to trick individuals into revealing sensitive information, such as passwords or financial details.
In today’s cybersecurity landscape where attackers are more innovative and persistent, an attack simulation helps to strengthen one of your weakest links, your people, in effectively defending your security perimeter against cyber threats.
What are the benefits of an attack simulation?
Phishing attack simulations helps to bolster an organisation’s cybersecurity defences and create a more informed and vigilant workforce.
Here are some of the top benefits of running an attack simulation:
- Enhanced employee awareness. Regular simulations help employees become more adept at identifying phishing emails and other social engineering tactics, reducing the likelihood of falling victim to actual attacks.
- Reduced risks. Organisations can significantly reduce their risk of data breaches and financial losses when employees can recognise phishing attempts, thereby helping to safeguard sensitive information and intellectual property.
- Realistic testing. Simulations mimic real-world phishing attacks, providing employees with practical experience in a controlled environment. Employees receive instant feedback on their actions, allowing them to learn from mistakes without real-world consequences.
- Identification of weaknesses. Simulations can reveal patterns in employee behaviour, highlighting areas where additional training may be needed.
Please contact to us to learn more about attack simulation for your Microsoft 365 environment.
Which service in Microsoft 365 includes the attack simulation?
Microsoft Defender for Office 365 Plan 2 (add-on license) or Microsoft 365 E5 includes the Attack Simulation training in the Microsoft Defender portal.
Microsoft Defender for Office 365 Plan 2 also includes everything in Plan 1 (email protection and collaboration features from zero-day malware, phishing, and business email compromise (BEC)) plus post-breach investigation, hunting, and response and automation.
Professional Advantage is a Microsoft Tier 1 CSP and can help you better optimise your licensing or set up an attack simulation for your Microsoft 365 environment.
Please reach out to us for more information.
How can you tell if an email is phishing?
Here are some of our pointers on how to spot a phishing email.
- Unusual, urgent request.
- Suspicious links or attachments.
- Dubious sender.
- Badly written email.
Read our pointers in more detail with specific examples on how a phishing email looks like as well as what to do when you encounter one in this blog.
Alternatively, you may call us at 1800 126 499 or email us at [email protected] if you need assistance with a cybersecurity incident.
What is Essential Eight and how does it protect my business?
Essential Eight is a baseline security strategy recommended by the Australian Signals Directorate (ASD) to protect businesses against cyber threats. It is composed of eight strategies:
- Application Whitelisting – prevents execution of malicious programs from automatically running by having a set of pre-approved apps.
- Application Patching – helps mitigate vulnerabilities on apps that need patching.
- Operating System Patching – allow you to mitigate vulnerabilities on operating systems that need patching.
- Restriction of Administrative Privileges – review admin privileges on specific IT systems and provide necessary permissions only for those who need them.
- Configuration of Office Macros – review Office macros and current policies to prevent untrusted macros with malware from automatically running.
- Application Hardening – ensure that unauthorised applications such as Adobe Flash Player or Java applets will not be utilised in browsers that have been known to deliver malware.
- Multi-Factor Authentication – use a second factor such as a physical token or mobile device to authenticate user access.
- Review Backups – ensure regular backups of data so you can get it back in case you suffer a cyber-attack.
These eight strategies, when implemented correctly, can greatly assist in defending against common cyber threats.
Understand further what is Essential Eight, why it's important and its maturity levels in this video.
Other resources you might be interested in:
Why is Application Whitelisting important?
Application Whitelisting focuses on going through a process of creating a list of applications required by the business, based on various user roles and activities, which effectively means that any unapproved applications (which includes malicious code that may have found its way into your environment) not part of the Whitelist will not work. It is part of the Essential Eight risk mitigation strategy by the Australian Signals Directorate.
Application Whitelisting is important for these reasons:
- It allows only trusted apps to run.
- It protects against zero-day attack.
- It reduces overall IT TCO due to the lesser effort required by IT to fix security issues.
We discussed in more detail why Application Whitelisting is essential for every business in this blog.
What is Managed Security Services?
The concept of Managed Security Services is very similar to a regular Managed Services where your IT environment is monitored and managed proactively by a third-party IT partner. Managed Security Services offers the same kind of arrangement but with more emphasis on intrusion detection, risk intelligence, and responding to security incidences.
Visit this page to learn more about our Managed Services.