Essential Eight
Baseline risk mitigation strategy recommended by the Australian Cyber Security Centre (ACSC) for reducing the impact of cyber security attacks.
Is your IT strategy based on an industry-recommended security model?
We live in an era where the digital apps and services that organisations use to serve customers and generate revenue are also what cyber criminals target to carry out their crimes. Hence, it is imperative that organisations, especially small to mid-size, have a foundational cyber security strategy to prevent malware delivery and limit the impact of cyber security attacks.
A complacent cyber security strategy can result in a hefty financial loss, tarnished brand reputation, unrecoverable loss of data, and customers leaving your business. A good way to mitigate your risks is to follow what the Australian government recommends as a baseline cyber security risk mitigation strategy called Essential Eight.
Mitigate your risks with Essential Eight
Essential Eight is a cost-effective cyber security risk mitigation strategy developed by the Australian Cyber Security Centre (ACSC) to help organisations reduce the risk of malware delivery and execution and limit the extent of cyber security incidents. It’s eight controls outline the risk mitigation strategies as follows:

Allow only trusted and approved applications to run on your network. This prevents execution of malicious programs from automatically running by having a set of pre-approved apps.

Determine patching procedures and levels for popular web browsers, Microsoft Office, Oracle Java, and PDF viewers. This helps mitigate vulnerabilities on apps that need patching.

Review office macros and current policies to prevent untrusted macros with malware from automatically running.

Ensure that unauthorised applications such as Adobe Flash Player or Java applets will not be utilised in browsers that have been known to deliver malware.

Review admin privileges on specific IT systems and provide necessary permissions only for those who need them.

Determine existing patching systems, patching schedules, and server/workstation patching compliance. This should allow you to mitigate vulnerabilities on operating systems that need patching.

Use a second factor such as a physical token or mobile device to make it more difficult for cybercriminals to access your systems, even when the password has been breached.

Ensure regular backups of data so you can get it back in case you suffer a cyber-attack. Determine RTO/RPO, retention period, online/offline backups, offsite storage location, and test restoration schedule.
Essential Eight Maturity Levels
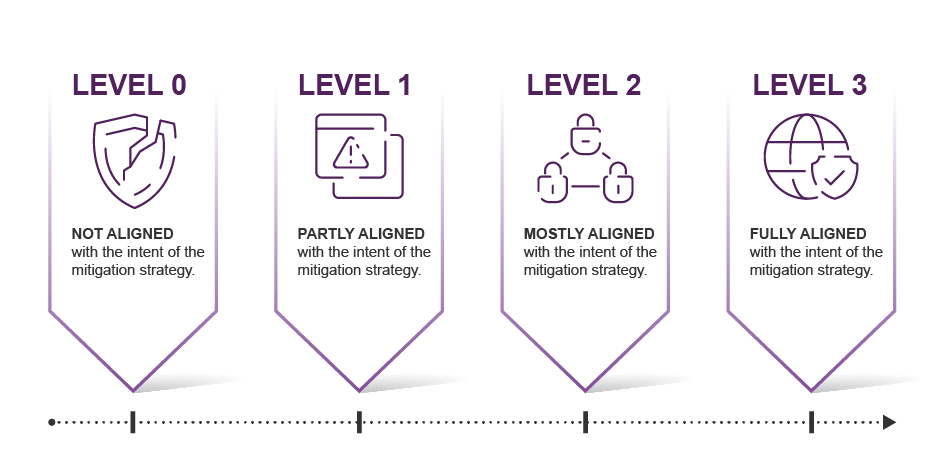
This signifies a significant weakness in your organisation’s overall cyber security posture that, when exploited, could facilitate data loss, compromise data integrity, or cause non-availability of your systems.
Cyber criminals who opportunistically seek common weaknesses in multiple targets rather than focusing on one specific target is the main focal point of this level. This is where they employ social engineering techniques to trick users into weakening the security of a system and then launch malicious applications.
This level focuses on cybercriminals with a modest step-up in capability from level one. Attacks will be more targeted and will use advanced tools to bypass security controls. Tools and techniques in their arsenal include compromising credentials using phishing, implementing technical, and social engineering to bypass weak MFA.
This level focuses on adversaries that are more sophisticated and do not rely on conventional tools and techniques. They exploit weaknesses in their victim’s security posture to magnify their access, avoid detection, and gain a strong footing on the system. Generally, cybercriminals will focus on specific targets and will invest time and effort to circumvent particular policies and controls.
Unlock the Benefits of Essential Eight Risk Assessment

Identify and mitigate known security vulnerabilities by employing a multi-layered and comprehensive approach to cybersecurity.

Ensure rapid containment and swift recovery from a security breach, allowing your company to maintain uninterrupted operations.

Utilise a quantitative benchmark to measure your organisation’s cybersecurity risk and ensure compliance with the Australian Signals Directorate’s recommendations.

The Essential Eight's low-cost, robust mitigation strategies are a smart investment, significantly reducing the financial impact of a potential cyber breach on your business.
Our Essential Eight Consulting Services

This service is for organisations that are new to Essential Eight and want to benchmark their current security posture against Essential Eight's maturity model. We will help you evaluate your existing systems, identify gaps in your current security controls, and provide advice on improving your organisation's security posture.
Sign up for Free Scoping
This service is for organisations that have already implemented some of Essential Eight's controls but are unsure about how well they compare against its maturity model. It is for businesses that want to achieve maturity levels 1, 2, or 3. We will help you identify a suitable maturity level for your environment and plan an implementation strategy to achieve it.
Consult with usAssess your cyber security risks.
Complete the form below, or contact us on 1800 126 499 to speak to one of our experts today.
Helping to secure and modernise Australian workplaces
Professional Advantage has more than thirty years of history delivering Microsoft solutions and services, and is one of a handful of multi-skilled Microsoft Solutions Partner and Tier 1 CSPs operating in Sydney, Melbourne, Brisbane, and Perth. We have worked collaboratively with hundreds of Australian organisations in helping them achieve a secure and modern workplace by leveraging Microsoft 365 and Azure.
average client retention
consistently high net promoter score
employees across 7 offices worldwide
solid experience in the IT industry, helping organisations achieve more from technology
Microsoft Solutions Partner for 6 designations and a Tier 1 CSP
Strong delivery practice across Microsoft’s 3 clouds: Dynamics 365, Microsoft 365, and Azure
Professional Advantage has earned a Microsoft Solutions Partner designation for proficiency in Microsoft Cloud, Modern Work, Business Applications, Data & AI Azure, Infrastructure Azure, and Digital & App Innovation Azure.

Explore more of our Cyber Security Services





Recommended resources for you







